Do you have what is needed for a successful implementation of DLP technology?

Information security relates to data
The proper use and protection of information lies at the core of the entire information and cybersecurity domain. And information is generated when working with data. It is therefore quite clear that everything in the information security domain relates to data. But data is not just a target for cybercriminals. It can also be used very effectively to achieve the right balance between security and usability. After all, the average total cost of a data breach globally in 2022 hit the highest level in the history of its report, increasing by $0.11 million to $4.35 million.
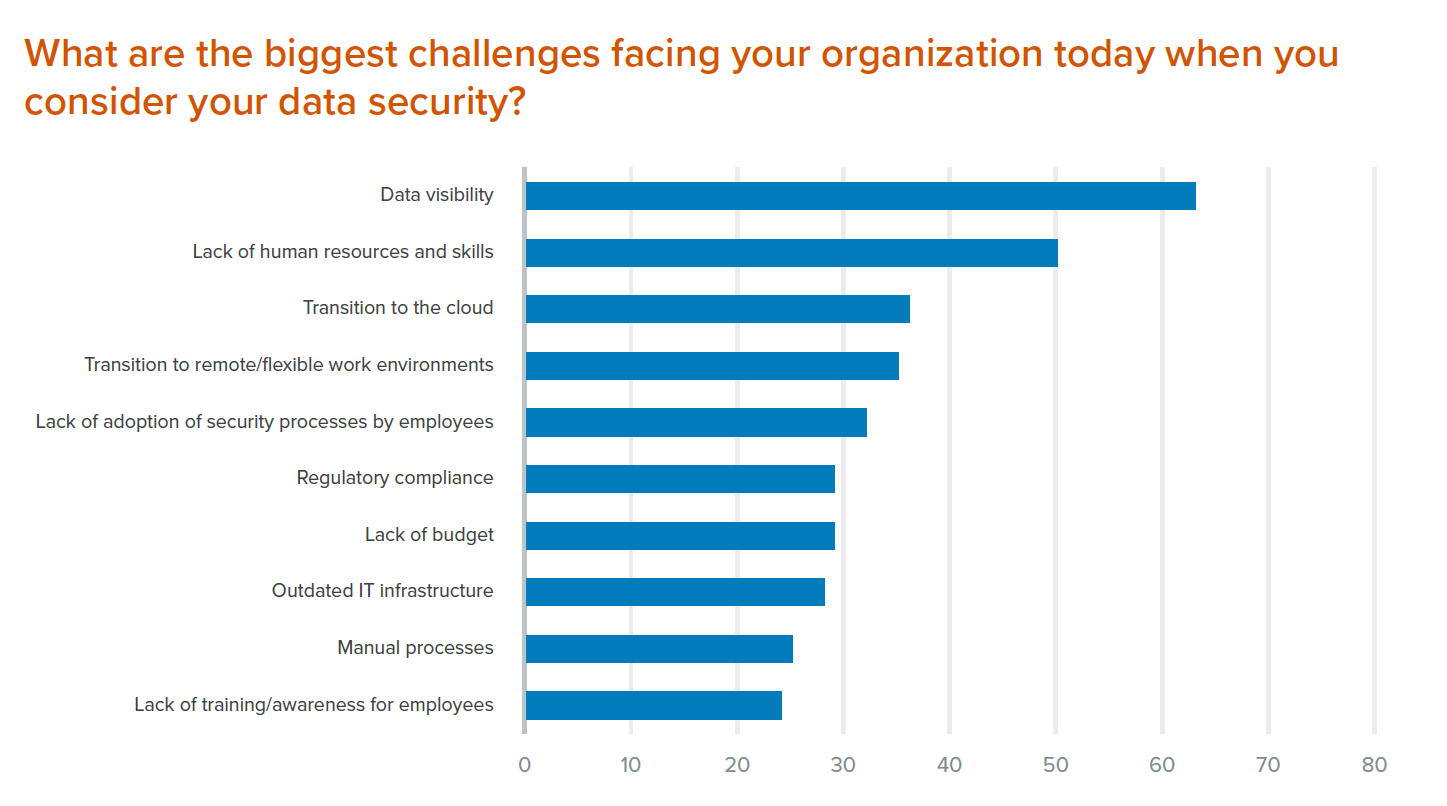
It is essential to understand how data is used in the organization in order to properly protect it from malicious actors and even insiders. Yet this is easier said than done. A recent survey conducted by iSMG and helpsystems found that most CISOs (63%) lack proper visibility into where data is located within their organizations, and a similar number (64%) are concerned that sensitive customer data could be compromised in the event of a breach.
It is therefore no surprise, that according to the same survey, most companies plan to make significant investments in enterprise data loss prevention (DLP), data classification and encryption.
Challenges to DLP-projects
In many cases, DLP technology can indeed help organizations understand their data better and thus protect it more efficiently. Nevertheless, the last 10+ years have shown that such a task can be quite challenging, regardless of the technology.
Let’s look at a few factors that could make DLP projects difficult to implement.
- Insufficient understanding
This is probably the main reason why DLP projects are often perceived as unsuccessful. Most solution providers and implementation partners do not take the necessary time to explain to their customers the process and to define the requirements and what should be expected. As a result, customers often assume that the technology they are acquiring will do most of the work alone. But as with any technology, it’s just a tool that makes someone’s job easier. Hence, that “someone” must be there to operate the tool.
- Low maturity
Implementing DLP solutions requires a certain level of maturity of the company’s security. This mainly concerns ensuring that rules and processes are in place for handling the different types of data. If these are missing, the project is at risk. Both customers and their implementation partners must be aware of this and plan accordingly.
- Inadequate planning
Planning of solution implementation is often considered only from a technology point of view. A few days for shipment, a few days for kick-off and alignment, a few weeks for implementation and finally a training and knowledge transfer. In DLP projects, this approach leads to disappointment and failed expectations. What must be included unquestionably is time to help customers define certain rules and policies within their organization, as this will help them understand what is required to leverage the technology in a meaningful way. It is essential to take a phased approach and include what is known as “learning mode” in the planning.
- Balancing knowledge and technology
DLP projects are one of the best examples of how focusing on technology and neglecting the human effort around it, or vice-versa, can lead to failure. Choosing the right technology is key to covering as much functionality as possible with a reasonable amount of manual work. But technology alone cannot address the different DLP use cases – you need company rules and policies for data management and the ability to enforce them without disrupting business processes and performance. A strong implementation partner who understands your business and has the experience to translate business rules into technology policies and settings is a prerequisite for a successful DLP project.
Considering the ever-increasing need to protect sensitive data from potential attacks, current and upcoming data protection regulations such as GDPR in the EU and its equivalents in other regions (CCPA, LGPD, PIPL, etc.), and the introduction of industry data security standards such as PCI DSI and the European Cyber Resilience Act, it is clear that we will see a growing demand for DLP Technologies in the near future. Are you ready to step into such a project?
Reach out to our experts at sales@gbs.com to understand how we help organizations to manage the complexity in such projects.
Author: Pavel Yosifov