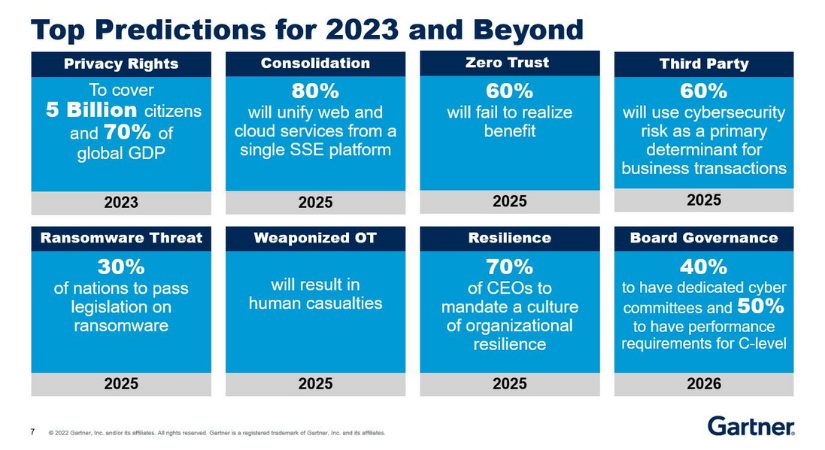
Threats and tendencies that will dominate cyber security in 2023

11 factors that will shape cyber security next year
Nobody really expects cyber attacks to decline in near future, but 2022 has finally brought some much-needed changes in the mindset towards cybersecurity. As thousands of people experienced the severe consequences of critical infrastructure breaches and disruption to public sector operations, it became clear that cyber security is not just a matter for the IT department, but affects the entire organisation. Moreover, to survive and remain competitive, a comprehensive long-term security strategy is required that goes beyond setting up a good firewall, securing endpoints and preparing incident response procedures.
The year 2022 saw political and financial turmoil, tightening of security regulations and a rise in the complexity and of number digitalisation instruments. Recent statistics indicate 28% more attacks in the third quarter (source: Check Point) than the year before. It is therefore more important than ever for companies around the world to reliably protect their employees and data, and gain visibility and control over security measures, while reducing costs and consolidating platforms.
Drawing on this evidence and their industry experience, the cybersecurity experts at DIGITALL and GBS (part of DIGITALL) spotlight the trends that are set to continue and forecast which threats will cause us the greatest concern in 2023.
Cyber threats in 2023
-
Ransomware
The number one cyber security threat for 2022 will neither disappear nor diminish in 2023. According to SCC Cyber, online searches for ransomware prevention methods soared by 300%. In other words: More and more companies have realised that ransomware can not only bleed a company dry financially, but also shut down its operations causing an existential crisis.
“An example of the shocking consequences of ransomware attacks on public administrative structures in Germany is the attack on DIHK, a county administration in Saxony-Anhalt. This triggered a state of emergency and citizen services such as parental allowance, unemployment and social welfare benefits, and vehicle registrations were unavailable or restricted for over 207 days,” said Dr Thomas Bruse, Senior Vice President at GBS.
With the advent of Ransomware-as-a-Service and the wide availability of hacking tools on the dark web, it is becoming easier for just about anyone with a Tor browser to carry out a ransomware attack. At the same time, hackers are shifting their focus to larger organisations, for which they are developing more targeted mechanisms that take into account specifics such as the industry, the company and its infrastructure. Alternatively, they subcontract their own ransomware to a specialised contractor who looks for lucrative targets that are most susceptible to this code.
On the other side of the front, we see a new trend – ransomware removal services. This service will gain even more attention in the coming year, as many companies who have fallen victim to the sophisticated social engineering do not have the knowledge and resources to set themselves free.
-
Email threats
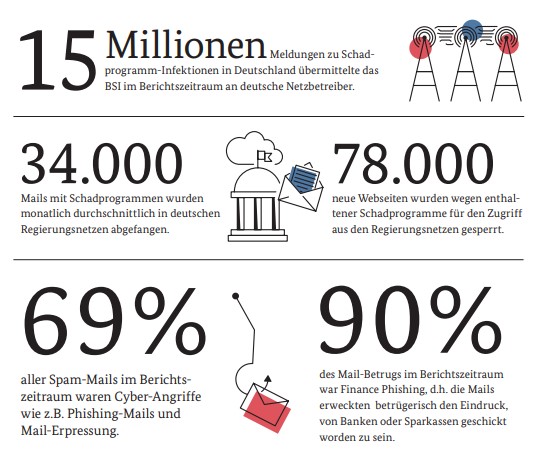
With email still the main communication channel, attempts to use it as a gateway are not expected to cease in the near future. Almost 70 % of the attacks are phishing and ransomware. As hackers shift to highly targeted social engineering and personalisation, the threats are becoming harder and harder to detect. The only thing that can stop an unsuspecting employee from opening a well-disguised email/attachment/link with malicious content is awareness. According to the BSI (Bundesamt für Sicherheit in der Informationstechnik), 34,000 infected mails are intercepted in government networks in Germany every month.
-
Destructive attacks on the rise
Apart from extortion for money, another strong motive for a breach is the theft of data or the destruction of systems. Recently, an increase in attacks aimed at deleting data, destroying infrastructure and seriously impairing operations has been observed. The cyber war in Ukraine has led to a record spike in DDoS campaigns, which will continue next year, as will geo-phishing. The pro-Russian hacking organisation Killnet, for example, specialises in carrying out DoS and DDoS attacks against governments (recently even against the EU Parliament’s website) and businesses to cause disruption.
-
Multifactor Authentication Scams
Multifactor authentication (MFA) was created as a protection mechanism against security breaches. Unfortunately, we are seeing more and more cases of hackers using it as a means to infiltrate. “The thrill of MFA is that once you log in, you gain access to various internal platforms and tools. There are already criminal organisations that focus on OPT1 passwords to violate MFA. For this purpose, proof of identity and man-in-the-middle attacks work quite well. A common approach, besides stealing credentials, is to use social engineering to trick the victim into sending the verification code to the criminals. MFA fatigue attacks, for example, exploit the “approve sign-in” notifications by sending countless sign-in approval requests to the victim until they finally give in.” explains Georgi Balev, Delivery Manager Security Operations at DIGITALL.
-
Work from home
When COVID triggered the big home office wave, businesses saw themselves exposed to unprotected personal devices and home networks. Unfortunately, this has not changed too much with hybrid working. Furthermore, the fact that many people still do not know their team members or partners was frequently exploited in the form of impersonation scams in 2022.
-
Political instability and false information
Government elections are expected to take place in more than 70 countries in 2023. Even without the Ukraine war, this is a major occasion for state-backed hackers to try to influence, manipulate, spy on or sabotage elections. Deepfakes (such as fake news and messages per email or over social platforms) are weaponized for spreading disinformation through all channels to shape people’s opinion and thus the election results.
-
IoT
Gartner estimates that by 2023 there will be 43 billion connected smart devices (from smart watches to smart cars) worldwide. The pressure to beat the market and launch a new device before the competition has left no time for vendors to address securing these devices. But even if no sensitive information is stored directly on them, criminals can still use them to monitor their victims or gain access to critical networks and devices. As incidents involving IoT devices increase, lawmakers around the world are on their way to tighten security requirements for cloud networks, connected devices, authentication and access restrictions such as encryption.
Drivers of cyber security in 2023:
-
Cloud solutions and third party vendors
In 2022, the investment focus for cloud solutions was on SaaS solutions and API security. “This is expected to not only continue, but also expand in the direction of governance and security – more visibility, control over security tools, and working only with third-party vendors that guarantee a sufficient level of security.” Pavel Yosifov Director Cyber Security Products at GBS said, “More and more solutions will gain XDR-like incident response capabilities and move towards CNAPP.”
According to Check Point, two-thirds of CISOs believe that reducing the number of vendors they have to work with will improve their security. A glance at the X-Force Threat Intelligence Index 2022 shows that 62% of organisations have fallen victim to a supply chain attack. Cutting complexity and workload by consolidating operations and security systems and selecting only security-certified vendors will reduce the risk of supply chain attacks, and provide more visibility and focus on vulnerabilities.
Source: BSI
-
AI
Artificial intelligence (AI) will continue to be deployed more frequently on both fronts. Its growing availability and capacity to automatically process large amounts of data in real time, faster and cheaper than any human, make it an invaluable aid to both cyber criminals and as a security tool. The market for AI products is expected to grow tenfold to $139 by the end of the decade. At the same time, IBM analysts have calculated that companies using AI to analyse traffic and detect potential threats have reduced their workload and saved about $3 million. This makes AI an excellent tool for industries that are forced to cut staff and costs.
Hackers use AI for the same reason, but for different purposes – to look for networks and devices with vulnerabilities and generate more targeted phishing emails without being detected by automated defences.
“Data will continue to be at the heart of businesses in 2023 and logically needs to be secured. However, locking up data can disrupt business processes. Using methods to understand, interpret and adequately control access to it in order to protect it will therefore remain a priority next year. AI and ML play a crucial role here.” comments Patrick Paulsen, Cyber Security Engagement Manager DACH at DIGITALL.
-
Lack of awareness
Several sources, including the World Economic Forum, confirm that 95% of successful cyber security breaches are the result of human error. Phishing and social engineering are involved in the majority of cases. This means that acquiring top-notch security technologies will not provide good protection if it is not accompanied by regular security awareness trainings for employees.
The year 2023 will be critical for many companies if they do not build and maintain a culture of awareness of vulnerabilities, protection of credentials and sensitive data, verification of payment information, and so on.
“Companies are going to turn more to SOCs (Security Operations Centres), as they allow an overview and monitoring of the entire security system. Secure application development technologies are another trend that will continue through 2023, as they make it possible to comply with rules and criteria, authorise penetration tests and even obtain a certificate for them.
I also think that many companies will find it more convenient to adopt Cyber Security as a Service (CSaaS), as it does not require them to build security teams with expertise and gives them the flexibility to reconfigure the services when needed. The same goes for CISO as a Service.” summarizes Yosifov his predictions for 2023.
-
Legislation
In 2023, we will see the adoption of more laws in different areas of cybersecurity. In the EU, the “rock star” will certainly be the Resilience Act, which will require vendors to accredit the solutions they offer to the European market in terms of security. The UK is also likely to update the NIST framework and hold vendors more accountable. While these are good steps in the right direction, there is still much to be done. Both at country level and as international legislation.
In particular, the fight against cybercrime at the international level is still very inefficient due to the lack of cooperation between countries. The falsification of IP addresses often makes it impossible to determine the country of origin of the attack and thus the jurisdiction. This allows hackers to escape the law by simply crossing borders.
Even though criminals are still one step ahead, both they and companies will continue to strengthen their position in 2023. Realising the need for a holistic cybersecurity strategy is making its way into executive floors, but the big security ramp-up is only just beginning.