New and more treacherous methods of ransomware attacks: intermittent encryption and how you can reliably protect yourself from it

The most frequently used gateway for cyber-attacks is still e-mail. That is where a never-ending technological battle between attackers and defenders is taking place. But despite big efforts by experts and ever greater investments by companies, the cyber criminals always seem to stay one step ahead. And they succeed because they develop hundreds of new malicious code versions every day and continue to refine their methods and attacks. Currently, cybersecurity experts hardly see themselves in a position to react quickly enough to all new zero-day attacks.
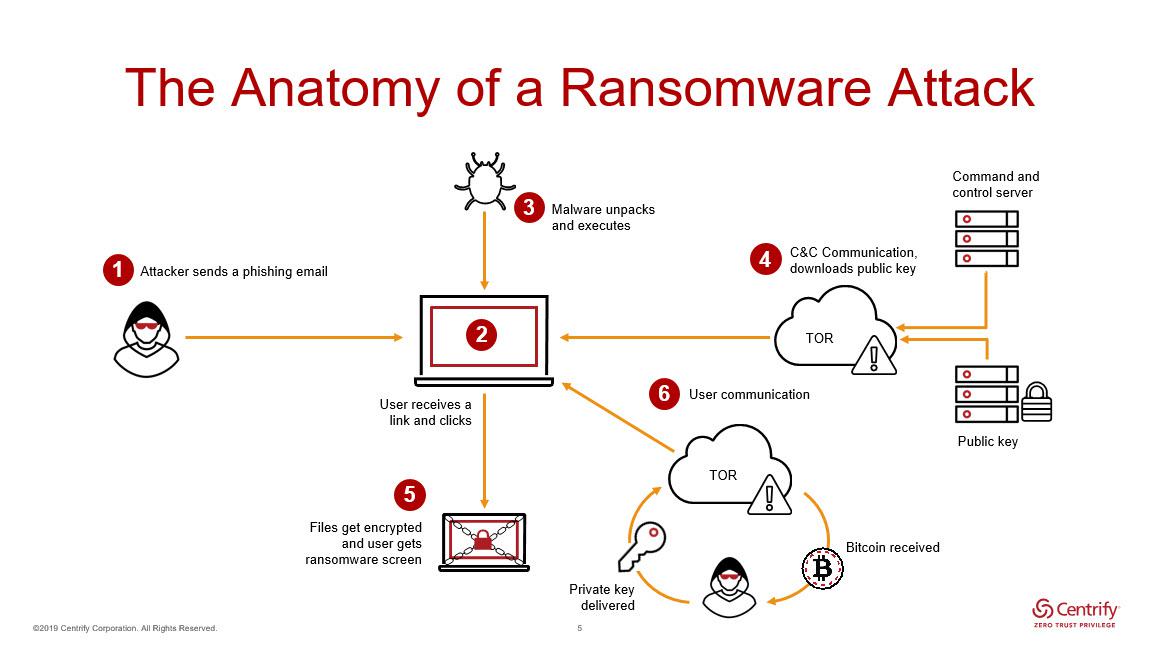
In this regard, ransomware has established itself as quite a lucrative “bread and butter” business for cybercriminals and is currently considered the biggest threat. The malicious code is easy to develop and there are enough unprepared companies and employees who can be effortlessly fooled by the attackers to open the doors for them. Once the malicious code has been infiltrated into a corporate network, it starts to analyse the infrastructure and spread. One would expect an attack to be sudden and immediate, but this is rarely the case. Instead, the malicious code tries to spread as inconspicuously and unnoticed as possible in the network. This phase can take several months.
How does intermittent encryption improve the efficiency of ransomware?
In the terminal phase, the actual attack begins – the encryption of the files and systems. In this phase, the attack is discovered sooner or later because the encryption changes files in large numbers and renders them unusable. The attacker therefore tries to encrypt a large number of files as quickly as possible before effective countermeasures can be initiated.
Source: Centrify
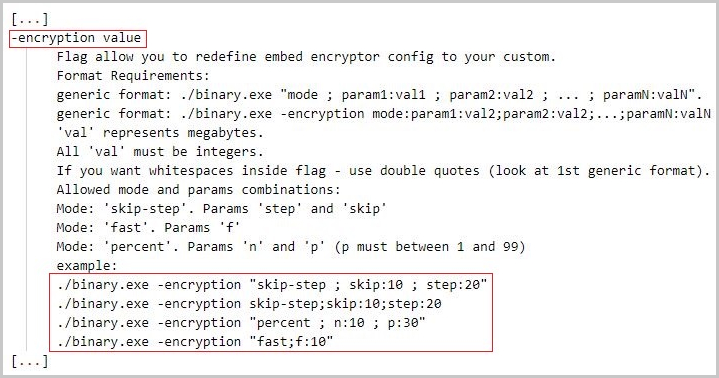
And this is precisely where the ransomware code has been optimised – current attacks increasingly employ a new technique, so-called intermittent encryption. In this case, the entire file is no longer encrypted, but only a few bytes of the file are partially encrypted. The advantage is that this considerably increases the performance of the malicious code. This means that more files can be encrypted per minute, which makes it much more difficult to effectively contain the attack. In this phase, indeed, every minute counts.
Furthermore, intermittent encryption renders the attack much more difficult to detect. Many systems for detecting attacks are based on statistical analysis methods that can recognise file manipulations. The challenge with intermittent encryption, however, is that the encrypted file appears unchanged at first glance. Since only a few bytes are encrypted, the change to the file is hardly noticeable. Often, the actual damage only becomes apparent when the file is opened.
How do you prevent a ransomware attack that uses intermittent encryption?
The implementation of intermittent encryption algorithms in ransomware once again gives attackers a clear advantage in the “cat and mouse game”. Moreover, we must assume that even more perfidious attack variants will soon be developed. Hence, at the moment, the only sensible recommendation to protect yourself against email attacks is: Do not allow any files to enter the company by e-mail that could potentially contain malicious code! But what does this mean for the company and for email communication?
Source: Sentinel Labs – Agenda customizable intermittent encryption
Many companies solve the dilemma by generally blocking e-mails with file attachments and not delivering them. Technically, this is easy to do. However, this often disrupts or at least hinders business processes, which has a negative impact on the performance of the company and the quality of service. To limit the negative effects, recipients can request blocked file attachments manually from the IT department. Manually checking and approving file attachments generates a lot of work for IT staff and seems counterproductive in times of staff shortages. It also passes the ball to the IT department, which now has to take responsibility for manually checking and approving file attachments. These approaches are therefore neither secure nor efficient.
Much easier and safer is to convert incoming file attachments into harmless file types fully automatically. One example of such a converter is the iQ.Suite Convert solution from GBS. It uses CDR (Content Disarm & Reconstruction) technology to automatically remove active code from file attachments and thus “disarm” the file. If desired, Office files can also be converted into PDF format, which provides additional security. This approach is thus completely independent of the analysis of a file attachment using an antivirus product.
Bear in mind: ANY analysis and evaluation can lead to a false result if the attack was only disguised well enough. GBS iQ.Suite Convert eliminates the code from every file attachment, completely independent of the evaluation by the antivirus analysis. What no longer exists can also no longer cause any damage. Thus, the converted and harmless file attachment can be delivered without delay and business processes are not affected.
Do you have questions about intermittent encryption or would you like to learn more about iQ.Suite Convert? Contact our team at sales@gbs.com and our experts will be happy to advise you.
Author: Dr. Thomas Bruse, Senior Vice President GBS